Moving security to the left has become a coined phrase meant to describe the process of getting the security team involved earlier in a process. Most typically, the phrase is used in conjunction with IT or software development projects. One of the top suggestions for ensuring security in a DevOps world is to move security to the left in the process tool chain. But what exactly or how exactly can you move security to the left?
Grab that Open Seat
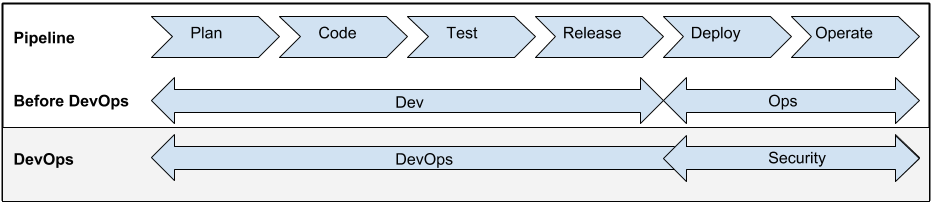
The new DevOps process pipeline created an opening for a seat at the table for security. Prior to DevOps, the development team owned the entire pipeline from plan to release. The Ops team would historically receive the release from over the wall and then be responsible for the deployment and operating the software inside the production environment. With the Ops team joining forces with Development in the process pipeline, that has opened a proverbial seat at the table. What I’ve started to witness are security teams taking advantage of the musical chairs to quickly grab the open spot.
Taking a seat at the end of the development pipeline is not enough. Too many security teams are still being relegated to positions too late in the process. While running pen tests and security code reviews after a release is better then nothing, its still not ideal. Security needs to find ways to add value to the process so they can act as a force for positive change instead of the after thought.
Threat Vector Analysis
Threat vector analysis is part science and part art and part trying to guess uncertainty. What is certain, however, is that most developers would rather be spending their time writing new functionality instead of trying to understand how an attacker could be break their code. The security team could offer a tremendous service to an organization by offering their expertise in this area.
Continuous Integration Security Testing
Continuous integration is a key component of DevOps. The security team can leverage the development chain to insert early yet important risk control tests. Those tests could be for example static or dynamic code analysis. Other tests could be simple yet known vulnerability checks in included libraries. The OWASP introduction to testing guide lists a plethora of application security tests that should be checked often and early.
Author Micro Security Services
Think about how great it would be if there was a group who specialized in authoring and delivering security related services into your application? Proponents of services models generally promote splitting the development team up into groups that are organized around business capabilities. For example, there are separate development groups for UI, middleware and DB. What’s missing in most of those models is who is responsible for security services such as authentication, authorization and audit. Security has an opportunity just waiting for them to add incredible value while also ensuring the security services used pass muster.
Summary
Where we once had Ops fighting their way to be part of the entire development process, we now have security trying to do the same. Ops managed to garner their way into the club by coming to the table with invaluable skills and resources. Now its up to security to present their creative sweet spot in order to secure their own seat at the table.
Further Reading
Andi Mann on Ensuring security and managing risk in enterprise DevOps