In this article, we will discuss the top five policies that organizations should implement to effectively govern their APIs during runtime. These policies are essential to ensure optimal API performance, security and alignment with evolving business and technical demands.
Beyond Design: The Importance of Runtime API Governance
When people think of API governance, design elements such as pagination or linting rules often come to mind. But true API governance goes much deeper — it must extend into the runtime environment to ensure APIs remain reliable and secure throughout their lifecycle. Neglecting these crucial aspects, such as performance monitoring, access control and security enforcement, can lead to significant production issues. Even a perfectly designed API is vulnerable if its runtime security measures are weak, potentially resulting in data breaches, financial losses or compliance violations. Similarly, without continuous monitoring, unexpected traffic surges can trigger outages, damaging user trust and business continuity.
API management teams are the backbone of runtime governance, tasked with enforcing policies around API deployment, version tracking, security and monitoring. Through centralized control via secure gateways, these teams ensure that APIs are consistently performing their best in real-world conditions — preserving their reliability and security long after the design phase.
But to truly excel in this critical role, these teams need a game plan. So, what does it take to ensure seamless runtime governance? What are some key policies that can transform good governance into great?
Five Must-Have Policies for Your API Teams
Recognizing the strategic importance of API governance, we highlight five essential policies for your API teams:
- Policy 1: Use a developer-friendly, traceable and easy-to-rollback approach for API deployments.
- Policy 2: Make comprehensive, correct API documentation available to users.
- Policy 3: Secure ingress and egress API traffic from malicious and unauthorized access.
- Policy 4: Provide precise API change impact analysis to minimize service failure and breaking changes.
- Policy 5: Provide proactive API monitoring and comprehensive, granular observability to reduce time to recovery.
Note on Terminology
‘Policy’ in this context refers to a high-level directive aimed at achieving specific outcomes, supported by standards. Standards are the detailed, actionable rules that help assess compliance and typically adhere to the IETF RFC-2119 guidance, using terms such as ‘MUST’, ‘SHOULD’, and ‘MAY’.
To learn more about Kubernetes and the cloud native ecosystem, join us at KubeCon + CloudNativeCon North America, in Salt Lake City, Utah, on November 12-15, 2024.
Policy 1: Use a Developer-Friendly, Traceable, and Easy-To-Rollback Approach for API Deployments
The 2024 State of Developer Experience Report found that 69% of developers lose over 20% of their time to inefficiencies. Engineering leaders highlighted better collaboration tools as one of the top five ways to boost productivity and satisfaction.
Effective API deployment is essential for agile development and rapid innovation. It requires a robust process that minimizes errors, facilitates collaboration and enables quick rollbacks. By storing API descriptions and configuration files in Git, organizations can establish a clear audit trail, making it easier to troubleshoot changes and roll back failures. Additionally, adopting a GitOps approach allows for declarative configuration management, automated updates and faster delivery of API changes.
A well-structured CI/CD pipeline is the backbone of efficient API deployments — as measured by the widely used DORA metrics assessing a software team’s performance. By automating the entire process, from code compilation to testing to deployment, organizations can ensure consistent quality, reduce manual errors and improve overall efficiency. This approach also fosters collaboration among development and operations teams, as the pipeline acts as a central hub for feedback and knowledge sharing.
Governance Standards and Metrics
- Standard 1.1: All API descriptions and configuration MUST be version-controlled in Git.
By managing API descriptions (such as OpenAPI) and API configuration files (such as Kubernetes Ingress manifests) in Git, organizations can create a workflow that provides a clear audit trail, recording changes, their timestamps and the responsible individuals. This traceability simplifies troubleshooting and enables easy rollbacks using a single Git revert command. It also empowers developers to edit files using their preferred tools, whether it is a text editor, CLI or other software.
Metric: Ratio of APIs under version control.
- Standard 1.2: All API configuration changes MUST follow a GitOps approach.
GitOps is a modern approach to managing application and infrastructure deployments. It involves storing the desired state of the system in Git repositories, which act as the source of truth. Declarative descriptions in formats such as YAML and JSON are used to represent this desired state. When configuration files are updated, continuous delivery tools synchronize the live state of the application with the desired state. This approach enables faster delivery of API changes and promotes collaboration through pull requests.
Metrics: Number of API configurations managed with GitOps and the API config change review speed.
- Standard 1.3: The CI/CD pipeline MUST act as the primary change agent, driving all changes, feedback and collaboration through automated processes, with no manual steps outside the pipeline.
A CI/CD pipeline is a series of automated processes that handle everything from code compilation and packaging to testing and deployment. It acts as a falsification mechanism and change driver, ensuring all changes are validated and comply with standards. By automating collaboration, the pipeline creates consistent, transparent feedback loops across teams. No manual steps should occur outside the pipeline, ensuring full automation and traceability.
Metric: Percentage of changes validated through the pipeline.
Benefits
Implementing this policy unlocks a host of powerful benefits. Teams can rapidly introduce new features and improvements with greater confidence, while ensuring a consistently high standard of API quality. Collaboration and knowledge-sharing between developers and operations teams become seamless, breaking down silos and fostering a more innovative work environment.
The risk of errors and disruptions is reduced, thanks to automated checks and streamlined deployment processes. Compliance with governance standards is not only easier to achieve but also sustainable over time, with every change leaving behind a clear and auditable trail. Together, these advantages create a more efficient, agile and secure API development process — empowering teams to innovate faster and manage APIs with confidence.
Policy 2: Make Comprehensive and Correct API Documentation Available to Users
Effective API management requires a comprehensive understanding of all APIs within an organization. This includes both documented and undocumented APIs, which can pose significant risks if left unmanaged. It is crucial to implement a robust API discovery mechanism and ensure accurate, up-to-date documentation.
Governance Standards and Metrics
- Standard 2.1: Edge technologies SHOULD detect undocumented APIs.
By monitoring network traffic at the edge, organizations can identify undocumented and unmanaged APIs, providing a first step in addressing API sprawl. Once detected, these APIs can be documented and added to the internal API catalog.
Metrics: Number of unmanaged APIs detected by edge controls, and the number of API description document defects.
- Standard 2.2: All live APIs MUST be documented in a central API catalog.
A central API catalog or registry is essential for storing and managing API documentation. This ensures that all APIs are easily discoverable and accessible to users.
Metric: Percentage of documented APIs in the API catalog versus the total number of APIs (documented and undocumented).
- Standard 2.3: The API management platform SHOULD support self-service onboarding.
To provide great developer experience, API management platforms should support self-service onboarding, allowing users to quickly request and obtain access to APIs.
Metric: Number of APIs documented in a self-service developer portal.
Benefits
By implementing these standards, organizations can gain visibility into API usage, improve developer experience, enhance API security, facilitate API integration, support business growth and improve overall API governance. This comprehensive approach to API management ensures that APIs are well-documented, easily discoverable and secure.
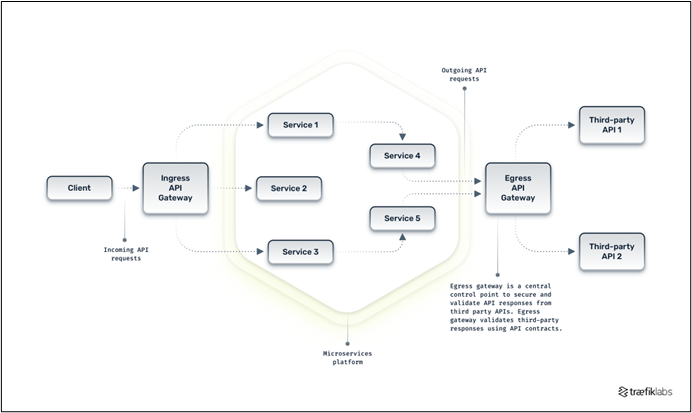
Policy 3: Secure Ingress and Egress API Traffic from Malicious and Unauthorized Access
The increasing use of APIs has expanded the attack surface for malicious actors. The 2024 State of API Security Report by Salt Security found that 95% of respondents faced security issues with production APIs, and 23% experienced a breach. Additionally, 25% expressed concerns that their API programs lacked adequate runtime or production security.
Organizations must secure both their own APIs and third-party APIs, such as those for LLMs, CRM systems and payment platforms. However, unsafe consumption of third-party APIs is an OWASP API Security Top 10 threat, occurring when external data is trusted without proper validation, leading to risks such as SQL injection, code injection, or data exposure.
To protect against security threats, organizations must implement strong runtime security measures for both their own APIs and third-party APIs.
Governance Standards and Metrics
- Standard 3.1: All governed APIs SHOULD be exposed through an API gateway configured with appropriate security controls.
An API gateway acts as a central point of control for API traffic, enforcing security policies such as authentication, authorization, rate limiting and input validation. By using an API gateway, organizations can centralize security controls, improve visibility into API traffic and reduce the risk of attacks.
Metrics: Number of governed APIs not exposed through the gateway, and the number of APIs with insufficient authentication.
- Standard 3.2: All public APIs MUST be protected by a WAF.
A web application firewall (WAF) is a security device that scans incoming HTTP traffic for malicious requests and blocks them in real-time. WAFs can use threat signatures and machine learning to detect and mitigate attacks, such as SQL injection, cross-site scripting (XSS) and DDoS.
Metric: Number of public APIs unprotected by a WAF.
- Standard 3.3: Third-party API traffic MUST be validated.
Consuming third-party APIs introduces risks if data is not properly validated and sanitized. Using an API gateway as an egress gateway can help ensure that third-party traffic complies with contracts and prevents data exposure. By validating third-party API traffic, organizations can reduce the risk of data breaches and ensure that their applications are not vulnerable to attacks.
Metric: Number of unvalidated third-party APIs.
Benefits
Implementing these standards can significantly enhance your API security posture. By shielding APIs from common attacks and unauthorized access, teams can prevent costly data breaches and ensure compliance with key regulations. Validating and sanitizing third-party API traffic mitigates the risk of security vulnerabilities, while centralized security controls through an API gateway enhance visibility and streamline management. Rate limiting and performance optimization techniques further boost API performance, preventing abuse and ensuring scalability.
Policy 4: Provide Precise API Change Impact Analysis to Minimize Service Failure and Breaking Changes
Effective API change management requires a thorough understanding of the potential impacts of changes on the overall system. By conducting change impact analysis, organizations can identify affected components, assess risks and prevent stability, performance and security issues.
Governance Standards and Metrics
- Standard 4.1: All API configuration changes MUST pass static checks.
By storing API configurations in version control and using GitOps, organizations can perform static analysis on API configuration in the CI/CD pipeline. This helps prevent misconfigurations and provides teams with a better understanding of the scope of their changes.
Metric: The ratio of the organization’s APIs whose configuration is under version control and change impact analysis checks.
- Standard 4.2: All APIs MUST follow the recommended versioning scheme.
API versioning is essential for managing API evolution and facilitating the introduction of new versions without disrupting existing integrations. Organizations should choose a versioning scheme that best suits their requirements and ensure that their runtime infrastructure supports it. By defining and adopting a consistent versioning mechanism, API providers can provide users with a clear migration path and effectively manage the API lifecycle.
Metric: The number of APIs that do not follow the versioning scheme.
Benefits
Change impact analysis helps identify potential conflicts and breaking changes, reducing the risk of service disruptions. API versioning ensures that APIs evolve smoothly and reliably, preventing stability and performance issues. By identifying issues early in the development process, development costs can be reduced and customer satisfaction enhanced through the minimizing of disruptions.
Policy 5: Provide Proactive API Monitoring and Comprehensive, Granular Observability to Reduce Time to Recovery
Effective API monitoring and observability are essential for maintaining API performance, detecting issues early and reducing recovery time. API monitoring tracks performance metrics such as response times and error rates, while API observability goes further by enabling troubleshooting and understanding system behavior. Observability relies on telemetry signals — metrics, logs and traces (MLT) — which allow API publishers to analyze and trace requests across distributed systems for debugging and system health insights.
API observability should follow open standards, such as OpenTelemetry, for collecting and exporting telemetry data. These standards ensure compatibility with various analytics platforms, prevent vendor lock-in and offer a common framework for cross-application troubleshooting.
Governance Standards and Metrics
- Standard 5.1: Teams MUST provide dashboards and configure alerts to monitor API request rate, error rate and request latency.
By monitoring key performance indicators, organizations can gain insights into API usage, identify potential issues and proactively address problems before they impact users.
Metric: The number of APIs not set up for monitoring.
- Standard 5.2: APIs SHOULD use OpenTelemetry to publish telemetry data.
OpenTelemetry is a widely adopted open-source observability framework that provides a standardized way to collect and export telemetry data. By using OpenTelemetry, organizations can ensure compatibility with various analytics platforms and avoid vendor lock-in.
Metric: The ratio of APIs instrumented with OpenTelemetry versus those that are not.
- Standard 5.3: API deployments SHOULD emit telemetry data.
Correlating application performance telemetry with API deployment events can help identify and address issues related to new deployments. This technique enables teams to quickly visualize and investigate performance problems and roll back changes if necessary.
Metric: The ratio of API deployment pipelines that publish telemetry data.
Benefits
By implementing these standards, organizations can proactively monitor API performance, detect and resolve issues quickly, gain deeper insights into API behavior, ensure compatibility with various analytics platforms and improve incident response. This comprehensive approach to API monitoring and observability enables organizations to maintain high API performance, reduce downtime and deliver superior user experience.
In Conclusion
Runtime API governance is no longer optional — it is essential for maintaining secure, reliable and scalable APIs in today’s digital landscape. These five policies form the foundation of a comprehensive runtime API governance strategy, allowing organizations to confidently scale their API ecosystem while minimizing risks and maximizing value.
| This article was contributed to KubeCon by Traefik Labs. By offering cloud-native, GitOps-driven API runtime solutions for demanding DevOps and platform engineers with diverse use-cases, environments and deployment models, Traefik Labs enables you to run your APIs easily, from anywhere.
We look forward to meeting you at KubeCon 2024!
|