Throughout my tenure as a DevOps cloud solutions architect, I’ve consistently observed a profound and persistent challenge in modern cloud environments: the relentless, yet often insidious, phenomenon of configuration drift. While change is an inherent and necessary component of agile development, its uncontrolled proliferation subtly erodes infrastructure integrity. Configuration drift, the divergence of deployed infrastructure from its source-defined configuration, has emerged as a critical vulnerability, particularly within the complex AWS environments I’ve managed, orchestrated by infrastructure as code (IaC) tools like Terraform.
The genesis of drift is multifaceted: Whether it’s manual edits in the AWS Console, stealthy shadow automation scripts deployed by independent teams or ad hoc emergency fixes executed under pressure. These seemingly isolated actions can bypass established CI/CD pipelines, introduce critical security vulnerabilities or violate stringent compliance mandates, all without immediate detection. For enterprises operating in highly regulated sectors such as finance, healthcare and government, where I’ve delivered solutions, the repercussions of undetected drift can be catastrophic, leading to data breaches, service outages and severe regulatory penalties.
While traditional DevOps practices have undeniably revolutionized cloud provisioning and management, my experience has shown they offer limited real-time protection against this creeping entropy. Terraform’s plan command, while essential for pre-deployment validation, only reveals drift during a subsequent deployment attempt. AWS CloudTrail and AWS Config provide invaluable audit trails and configuration snapshots, but often alert after the drift has occurred, leaving a critical window of vulnerability. What I identified as conspicuously absent from the current paradigm was a layer of proactive, contextual and automated intelligence for drift detection, seamlessly integrated and powered by artificial intelligence (AI)
The Challenge: Why DevOps Alone Falls Short
Despite significant advancements in IaC, CI/CD methodologies and sophisticated monitoring solutions, the efficacy of current drift detection mechanisms is fundamentally constrained. From my vantage point, today’s approaches are largely:
- Reactive, not proactive: Detecting issues after they have manifested, rather than anticipating or preventing them.
- Fragmented: Requiring manual correlation across disparate tools, logs and dashboards, a laborious process I’ve seen consuming countless engineering hours.
- Context-blind: Lacking the ability to differentiate between an intentional, business-approved modification and an unauthorized, rogue alteration. This often leads to alert fatigue or, worse, missed critical events.
- Manual and Opaque: Often leaving developers unaware of the broader implications of untracked, ad hoc changes.
I’ve personally witnessed the pitfalls of reactive drift detection, such as a critical instance where a developer’s manual deletion of an S3 bucket via the AWS Console went unnoticed for days in a high-stakes environment, nearly leading to irreparable data loss until our subsequent Terraform plan execution revealed the discrepancy. Such incidents underscored for me the absolute necessity of integrating real-time intelligence into infrastructure governance.
Solution Overview: An AI-Augmented Drift Detection Framework
To transcend the inherent limitations of current practices and establish a truly resilient cloud infrastructure, I spearheaded the conceptualization and development of an innovative, end-to-end framework. This architectural paradigm cohesively integrates foundational IaC capabilities with cutting-edge artificial intelligence and machine learning (AI/ML):
- Foundational Drift Detection: Leveraging Terraform state differences (terraform show) and comprehensive AWS Config snapshots to establish a robust baseline of configuration integrity.
- AI/ML-Driven Anomaly Classification: Employing advanced AI/ML models for sophisticated anomaly classification, outlier detection and dynamic risk scoring of identified divergences. This goes beyond simple diffs to understand the significance of a change.
- Natural Language Processing (NLP) Intent Analysis: Utilizing NLP engines to infer the context and intent behind changes by analyzing commit messages, pull request descriptions and associated ticketing system entries, a crucial layer of human context.
- Automated Remediation Pipelines: Implementing intelligent, automated workflows to proactively propose or execute immediate fixes, minimizing exposure and ensuring rapid restoration of the desired state.
“My work is driven by a core principle: instead of relying on post-mortems, we must enable drift forensics in real time, proactively safeguarding infrastructure integrity.”
Implementation Guide: Step-by-Step Architecture
Implementing this AI-augmented framework involved a structured approach, integrating established cloud-native services with advanced AI capabilities. I designed and oversaw the architecture of each component:
Step 1: Unify Drift Signal Collection: I established a comprehensive data pipeline for continuous configuration capture, crucial for building our baseline:
- Regularly executing Terraform show commands within our CI/CD pipelines and persisting the JSON output to a secure Amazon S3 bucket.
- Configuring AWS Config to capture continuous configuration history and snapshots across all relevant AWS resources. This provides a crucial, independent baseline against which to compare Terraform state.
Step 2: Intelligent Comparison and Detection: I designed a serverless function (e.g., AWS Lambda) equipped with a robust diff parser (such as hcl-diff for Terraform or custom logic written in Python) to programmatically compare the collected Terraform state with AWS Config snapshots. This process precisely identifies configuration mismatches.
Step 3: Feed into Anomaly Classifier: A key innovation I introduced was the integration of identified drifts into a trained AI/ML model. This model, which I developed and deployed in Amazon SageMaker, is specifically engineered to:
- Detect anomalous spikes in critical resource changes (e.g., IAM policy alterations, network ACL modifications) that deviate significantly from historical patterns.
- Classify specific types of drift, such as unauthorized tag deletions, changes in EC2 instance types or non-compliance with security group ingress/egress rules, assigning a severity level to each.
- Score the perceived risk of each drift event based on its impact, resource criticality and historical context.
Step 4: Run NLP Intent Parser to provide invaluable human context: I integrated an NLP engine utilizing pre-trained Natural Language Processing (NLP) models (e.g., fine-tuned models from HuggingFace, such as DistilBERT, deployed on Amazon ECS). This engine analyzes:
- Git commit messages from associated code repositories.
- Descriptions within Pull Requests (PRs).
- Linked Jira tickets or other change management records. This step aims to infer the intent behind changes, helping differentiate approved, documented modifications from rogue or undocumented actions.
Step 5: Trigger GitOps Remediation: I established an automated remediation pipeline based on the GitOps principle. Upon detection of unauthorized or high-risk drift, the system I designed can:
- Auto-generate and submit GitHub Pull Requests (PRs) that propose the necessary Terraform state corrections or infrastructure rollbacks, complete with detailed explanations.
- Optionally, integrate with GitOps deployment tools such as ArgoCD or Spinnaker to automatically apply approved remediations, ensuring the infrastructure converges back to the desired state defined in Git with minimal human intervention.
Step 6: Maintain DriftOps Console to provide comprehensive visibility and control: I oversaw the development of a centralized, intuitive dashboard (e.g., using React for the frontend, FastAPI for the API and PostgreSQL for data storage) to serve as a ‘DriftOps Console’. This console provides:
- Real-time drift timelines and historical trends.
- Visual comparisons between the desired Terraform state and the live AWS configuration.
- A comprehensive, immutable audit trail of all drift events, their classifications and remediation actions.
Tooling Landscape: What’s Available and How They Compare
From my comprehensive analysis, a truly modern drift detection stack necessitates a synergistic combination of purpose-built tools:
Tool | Strength | Limitations |
| Driftctl | Terraform-aware drift checks, open-source | No integrated ML for anomaly detection or UI |
AWSConfig | Native AWS integration, real-time snapshots | Not directly Terraform-aware, post-facto alerts |
| CloudQuery | SQL-based queries & custom reporting | Complex real-time monitoring setup for drift |
| Steampipe | Interactive dashboards with SQL, compliance | No native AI/NLP integration for contextual analysis |
The optimal solution, which I champion, combines the IaC awareness of Driftctl with the foundational compliance baselining of AWS Config, crucially augmented by custom-built AI/NLP modules for intelligent anomaly detection and contextual understanding. This layered approach is precisely what yields superior results.
Real-World Case Study: Global Fintech Firm
Problem: In a recent engagement with a leading global fintech firm, I was tasked with addressing a critical issue: maintaining configuration consistency across their expansive AWS footprint. Specifically, security groups across over 200 AWS accounts were being frequently and manually modified outside of established Terraform workflows, leading to pervasive compliance violations and critical security exposures that were difficult to track and remediate.
Solution: I led the design and implementation of this AI-based drift detection framework for the firm. My solution involved:
- Developing and deploying custom Lambda functions for real-time correlation of CloudTrail logs with the authoritative Terraform state and Git history.
- Training an ML model in SageMaker to precisely identify patterns indicative of unauthorized security group changes, distinguishing them from legitimate, automated alterations.
- Utilizing a fine-tuned NLP model to analyze developer commit messages and Jira tickets, inferring the intent and justification for each change to minimize false positives.
The system I engineered autonomously flagged unauthorized security group changes, rigorously differentiated them from approved modifications, generated automated Pull Requests (PRs) for rollback and instantiated a streamlined review workflow for critical deviations.
Impact: The implementation, under my technical leadership, yielded transformative results, demonstrably enhancing the firm’s security posture and compliance adherence.
Metric | Before | After | Results |
Unauthorized Console Changes | ~40 per month | ~5 per month | 88% Reduction |
Terraform Plan Drift Alerts | Manual, ad-hoc | Automated, real-time | Continuous Detection |
Audit Readiness Score | Low, highly labor-intensive | High, auditable, immutable logs | 50% Faster Audits |
Average Time to Detect & Remediate Drift | Hours to days | Minutes | Substantial Improvement |
Visuals Walkthrough
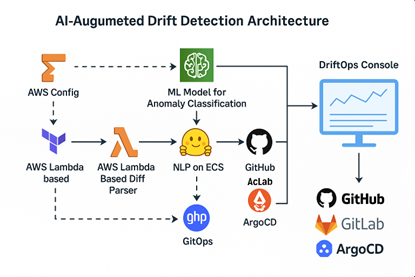
- 📌 Diagram 1: AI-Augmented Drift Detection Architecture: This diagram visually depicts the integrated flow of our framework, starting from AWS Config and Terraform state collection, feeding into an AWS Lambda-based diff parser. It shows the parsed data flowing into an Amazon SageMaker-hosted ML model for anomaly classification, followed by an NLP service (e.g., HuggingFace on ECS) for intent analysis. The output triggers GitOps workflows via GitHub/GitLab and a tool like ArgoCD for automated remediation. A centralized DriftOps Console provides a holistic view. This visual emphasizes the seamless, closed-loop feedback system that differentiates my approach.
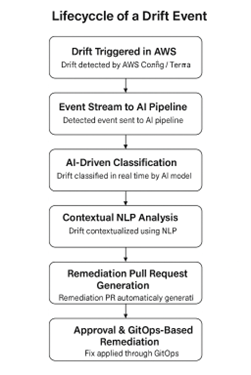
- 📌 Diagram 2: Lifecycle of a Drift Event: This sequence diagram breaks down the journey of a single drift event from its occurrence in AWS to its complete resolution. It illustrates the automated detection by AWS Config/Terraform, the real-time classification by the AI model, the contextualization through NLP, the automated generation of a remediation PR and the final application of the fix through GitOps. This visual highlights the speed and automation inherent in my solution compared to traditional manual processes.
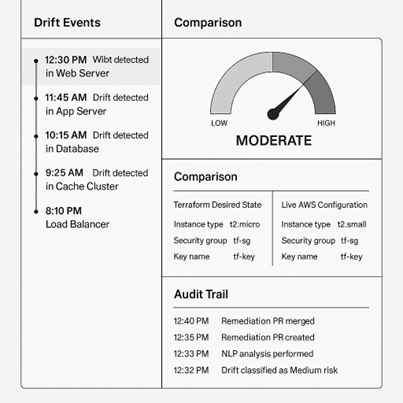
- 📌 Diagram 3: DriftOps Console Mockup: This visual presents a conceptual user interface of my DriftOps Console. Key elements include a timeline view of drift events, a side-by-side comparison pane showing Terraform desired state versus live AWS configuration, a dynamic risk-scoring dashboard and a comprehensive audit trail of all actions taken. It underscores the unparalleled comprehensive visibility and control gained by operations teams.
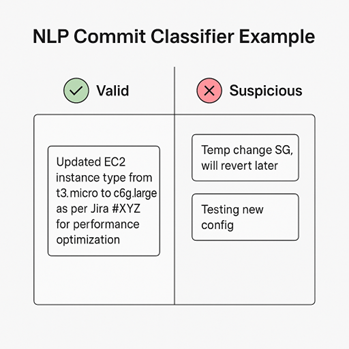
- 📌 Diagram 4: NLP Commit Classifier Example: This diagram showcases concrete examples of commit messages or Jira descriptions and how my NLP engine classifies them. It demonstrates how a ‘Valid’ change (e.g., ‘Updated EC2 instance type from t3.micro to c6g.large as per Jira #XYZ for performance optimization’) is differentiated from a ‘Suspicious’ one (e.g., ‘Temp change SG, will revert later’ or ‘Testing new config’). This visual highlights the critical role of AI in discerning legitimate intent from potentially unauthorized or problematic changes.
Compliance Matters: A Must for Regulated Industries
For organizations in regulated sectors, drift is not merely an operational inconvenience; it’s a direct threat to compliance. My work directly addresses how undetected drift can lead to:
- Compromised data encryption standards.
- Unauthorized widening of IAM access permissions.
- Breaches of mandated tagging standards for cost allocation or security.
- Deletion or alteration of critical audit logs, undermining accountability.
- Non-compliance with industry-specific regulations (e.g., HIPAA, PCI DSS, and GDPR).
Key benefits of my AI-driven drift detection framework:
- 24/7 Continuous Monitoring: Proactive, automated surveillance eliminates human error and latency, ensuring constant vigilance.
- Enforced Policies with open policy agent (OPA): I’ve integrated policy-as-code to prevent non-compliant changes before they propagate, acting as a preventative governance layer.
- Immutable, Justifiable Logs: Provides an undeniable audit trail, crucial for rigorous regulatory reporting and forensic analysis.
- Reduced Manual Effort in Audits: Automated evidence collection and clear audit trails significantly streamline compliance audits, saving immense human capital.
- Enhanced Security Posture: Minimizes the attack surface by rapidly rectifying unauthorized configurations and enforcing security baselines.
Comparative Snapshot: Traditional vs. AI-Augmented
Capability | Traditional DevOps | My AI-Augmented Drift Detections |
| Drift Visibility | Periodic, manual or post-factor | Real-time, continuous, granular |
Change Context | Not tracked or manual correlation | NLP + rich metadata inference for intent |
| Risk Scoring | Absent or heuristic-based | ML-driven prioritization, dynamic risk scores |
| Remediation | Manual, often reactive, error-prone | Automated Terraform PRs, GitOps-driven |
| Compliance Support | Fragmented, relying on human diligence | Built-in enforcement, automated evidence |
Summary: The Future of Infrastructure Governance
The integration of AI into drift detection fundamentally transforms infrastructure governance. My AI-enhanced drift detection framework empowers DevOps teams to:
- Maintain continuous compliance: Ensuring infrastructure consistently adheres to regulatory and internal standards with minimal human oversight.
- Catch misconfigurations early: Preventing small deviations from escalating into major incidents by identifying them at inception.
- Automate root-cause analysis and rollback: Drastically reducing Mean Time To Recovery (MTTR) and minimizing operational disruptions.
- Prepare for audits with unparalleled confidence: Providing comprehensive, verifiable and immutable audit trails that meet the strictest regulatory demands.
This solution represents a paradigm shift, seamlessly blending the precision and immutability of IaC with the foresight and adaptive intelligence of ML. It transitions organizations from a reactive, firefighting approach to infrastructure problems to a proactive, intelligent governance model — a critical evolution for any enterprise striving for operational excellence and robust security in the cloud, a domain where I continue to drive innovation.




