ArmorCode, this week at the Black Hat USA 2025 conference, revealed it has extended its Anya artificial intelligence (AI) tool to generate suggested code fixes that are customized for specific runtime environments.
At the same time, ArmorCode is adding a software supply chain module to provide visibility into the usage of software components in a way that surfaces quality metrics, security posture assessments and health indicators to identify risks. The module also automates the generation of composite software bill of materials (SBOMs) via integration with the Vulnerability Exploitability eXchange (VEX) format that is needed to comply with, for example, the Cyber Resilience Act adopted by the European Union (EU).
Finally, ArmorCode has added support for the Model Context Protocol (MCP) developed by Anthropic to make the data collected and created using Anya accessible to external large language models (LLMs) and third-party query tools.
Mark Lambert, chief product officer of ArmorCode, said the overall goal is to make it simpler for application development and cybersecurity teams to collaborate using its application security posture management (ASPM) platform. The latest update to Anya now makes it possible to present application developers with suggestions for remediating a source code issue that is much more likely to actually work because of the context about the runtime environment that Anya has, he added.
The approach sharply reduces the time, effort and stress involved with patching an application in a way that ensures application developers are still able to review code before it is added to a code base, said Lambert.
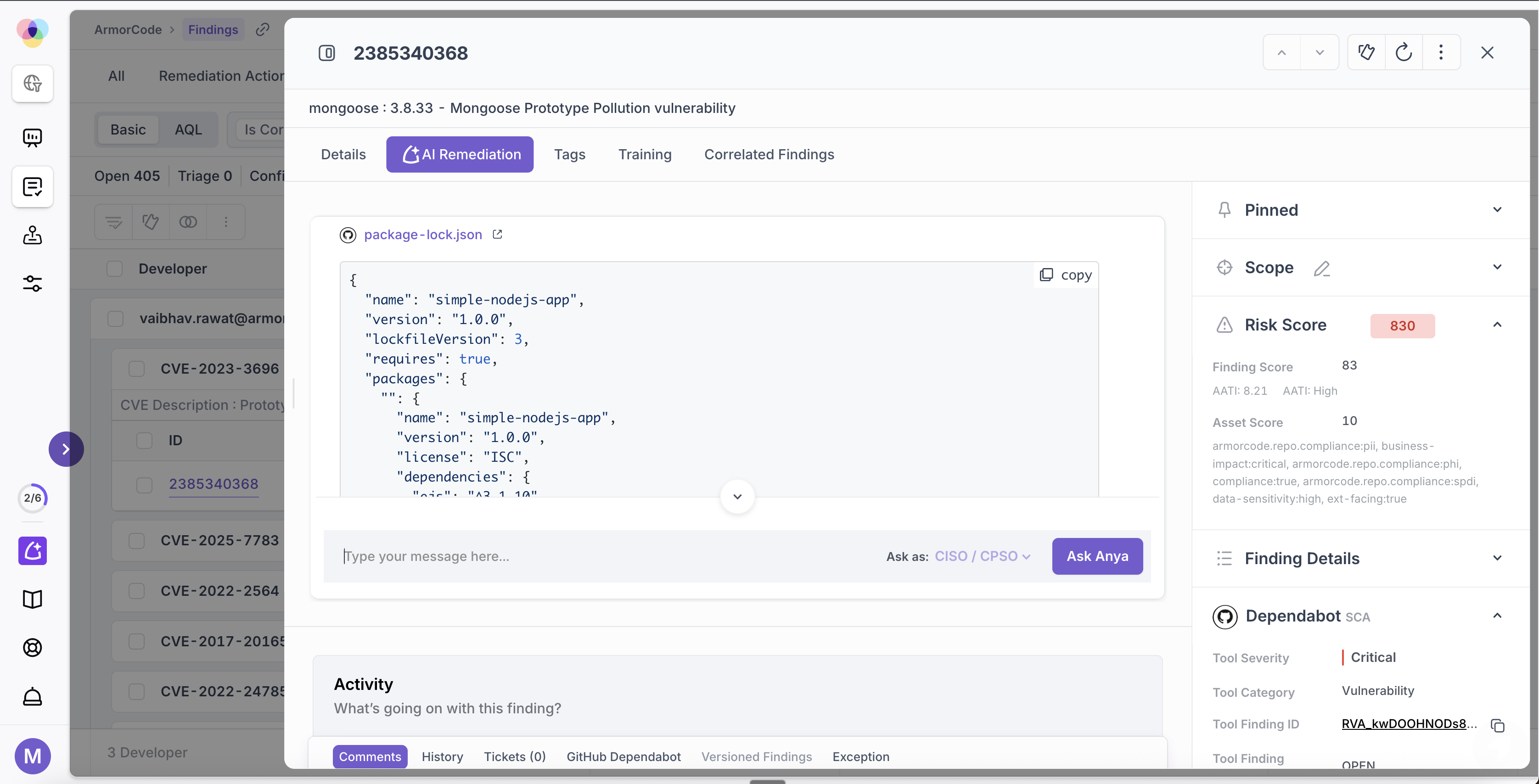
The Anya platform has been trained using data collected from more than 40 billion findings spanning 320+ integrations. Armed with those insights, Anya is now able to generate fixes to code that DevSecOps teams, depending on the complexity of the issue, can be automatically applied or reviewed, noted Lambert.
Being able to automatically apply patches will become increasingly critical as the overall size of the attack surface that needs to be defended continues to exponentially increase, he added. As application development teams continue to embrace AI coding tools, the pace at which applications are being deployed and updated will, in many cases, soon overwhelm DevSecOps teams unless they are able to automatically apply a much larger number of patches, said Lambert.
More challenging still, many of the AI coding tools being adopted are, at least in the short term, generating more vulnerabilities than ever to remediate simply because they were trained using flawed examples of code, he added.
It’s not clear to what degree organizations are prioritizing application security, but a recent Futurum Group survey finds nearly all the cybersecurity leaders surveyed are investing in software supply chain security, with application security posture management (ASPM) and DevSecOps automation and orchestration topping the priority list, followed closely by security composition analysis (SCA) tools, application programming interface (API) security and dynamic application security testing (DAST) tools. The survey also finds the source of the funding for these initiatives is becoming more of a shared responsibility, with only 21% of respondents reporting that security budgets are the sole source. In fact, half of the respondents (50%) noted that application development teams now own responsibility for application security.
Regardless of how DevSecOps initiatives are funded, the one thing that is for certain is that cybercriminals with each passing day are becoming more adept at discovering and exploiting vulnerabilities, so time to remediation is now more than ever a much more pressing concern.




