Abstract
The growing complexity of modern software development and the increasing speed at which organizations need to deliver software have led to the widespread adoption of DevOps practices, particularly continuous integration/continuous deployment (CI/CD) pipelines. These pipelines enable rapid development and deployment cycles; however, they also introduce significant security risks that must be addressed continuously. The traditional methods of integrating security, including DevSecOps, are often reactive and inadequate in keeping pace with change.
This white paper proposes the next evolutionary step in DevSecOps — the fully autonomous CI/CD pipeline, driven by artificial intelligence (AI) and machine learning (ML) technologies. By leveraging AI/ML, organizations can automate security throughout the software life cycle, from coding to deployment, enabling continuous, real-time security without manual intervention. This paper explores the integration of AI/ML into DevSecOps, the impact of this integration on security, agility and development speed, and the challenges and opportunities of such an autonomous system.
1. Introduction
As organizations move toward faster release cycles, integrating security into the software development process has become more critical than ever. The concept of DevSecOps — combining development, security and operations — addresses this need by embedding security directly into the CI/CD pipeline. However, traditional DevSecOps tools often rely on static rules and manual interventions that cannot keep up with the pace of modern development. With software becoming increasingly complex and cyber threats becoming more sophisticated, manual security checks and reactive responses are no longer sufficient.
Enter the concept of the fully autonomous CI/CD pipeline — a system where AI and ML technologies continuously monitor, detect and address security threats as code is being written, integrated and deployed. This paper will outline the potential of such systems and their role in ensuring continuous security in modern software development practices.
2. The Evolution of CI/CD and DevSecOps
2.1 What Is DevSecOps?
DevSecOps is the practice of integrating security into every phase of the software development life cycle, from design to deployment. In traditional software development, security is often treated as an afterthought or bolted on at the end of the development process. DevSecOps seeks to make security a continuous, integrated part of development, testing and deployment.
2.2 The Challenges of Traditional DevSecOps
While DevSecOps has improved security practices, there are still several challenges, such as:
- Manual Processes: Security checks are often manual and reactive, which can slow down development.
- Security Tools Integration: Many security tools are isolated from the development process and cannot keep up with rapid deployment cycles.
- Human Error: Developers and security professionals can miss critical vulnerabilities, particularly in large, complex codebases.
2.3 The Need for Automation
The rapid pace of modern software development demands more than just manual checks and delayed response times. Automation is required to address these needs. This is where AI and ML come into play.
3. The Role of AI and ML in DevSecOps
3.1 Understanding AI and ML in DevSecOps
AI and ML can be used to detect vulnerabilities, predict potential security risks and even automate remediation without human intervention. By training models on historical data, these technologies can:
- Identify Patterns: AI can recognize patterns in code that are indicative of vulnerabilities, such as injection flaws or insecure coding practices.
- Predict Risks: ML can use past attack data to predict where vulnerabilities are likely to occur in future code, reducing the attack surface.
- Automate Remediation: AI can automatically patch known vulnerabilities, reduce configuration errors and even block suspicious commits in real-time.

3.2 Benefits of AI and ML in the CI/CD Pipeline
- Real-Time Security: AI/ML can continuously analyze code as it’s being developed and integrated, ensuring that vulnerabilities are detected and addressed before they reach production.
- Proactive Threat Detection: Machine learning models can anticipate new security threats based on patterns in existing data, allowing for a proactive rather than reactive approach to security.
- Reduced Manual Intervention: With AI automating routine security checks and decisions, human security experts can focus on more complex tasks that require human judgment, such as strategic threat analysis.
- Scalability: AI/ML systems can scale with the growing complexity of modern software, managing more code, more integrations and more deployments with ease.
3.3 Examples of AI/ML in Security
- Code Scanning: AI-powered tools such as DeepCode analyze code at the commit stage to detect potential vulnerabilities.
- Automated Penetration Testing: ML models can simulate real-world attack scenarios to identify weaknesses in an application before it’s deployed.
- Anomaly Detection: ML algorithms can analyze network traffic and user behavior to identify abnormal patterns indicative of a cyberattack.
4. The Future of Fully Autonomous CI/CD Pipelines
4.1 What Is a Fully Autonomous CI/CD Pipeline?
A fully autonomous CI/CD pipeline goes beyond just automating the deployment process. It involves completely automating testing, security and deployment, and leveraging AI and ML to continuously monitor and protect every stage of the pipeline. This means:
- Code is analyzed and secured in real-time as developers commit changes.
- Automated security policies are enforced based on continuously evolving threat intelligence.
- Vulnerabilities are automatically fixed before they can be exploited in production.
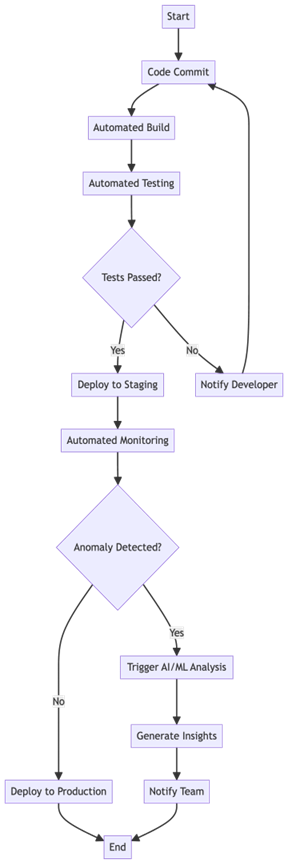
4.2 How It Works
A fully autonomous CI/CD pipeline incorporates the following steps:
- Code Commit Stage: As developers commit code, AI tools scan for vulnerabilities, check for insecure coding patterns and validate against security baselines. If a vulnerability is found, the pipeline can either block the commit or automatically suggest a fix.
- Build Stage: The pipeline builds the application, continuously monitoring the code for any security issues that may arise during the compilation process. ML can be used to predict and prevent issues by leveraging historical build data.
- Test Stage: AI and ML models automatically conduct tests to identify potential vulnerabilities that traditional static analysis tools might miss. Automated penetration tests and dynamic application security tests (DAST) are performed as part of this stage.
- Deploy Stage: Before deployment, the pipeline checks the code against security policies and compliance standards. AI can even simulate attack scenarios to ensure that the application is secure from real-world threats. If vulnerabilities are found, the system automatically halts the deployment and suggests fixes.
4.3 Continuous Security in a Fully Autonomous Pipeline
With AI/ML integrated into every stage of the CI/CD pipeline, security becomes a continuous process:
- Adaptive Security Policies: AI systems adapt security policies based on the changing landscape of threats, ensuring continuous protection without requiring manual updates.
- Self-Healing Pipelines: If a vulnerability is detected, the pipeline can automatically patch the code or rollback changes to prevent security breaches.
- Zero-Trust Architecture: AI models enforce a Zero-Trust model, ensuring that every part of the code and environment is continuously verified and authenticated.
5. Challenges and Roadblocks
While a fully autonomous CI/CD pipeline powered by AI and ML offers numerous benefits, some challenges persist:
- Data Privacy and Security: Ensuring that AI models do not inadvertently expose sensitive data during analysis is critical.
- Model Training and Accuracy: AI models need vast amounts of data to train and must be regularly updated to stay accurate. Poorly trained models can lead to false positives or missed vulnerabilities.
- Integration Complexity: Integrating AI and ML tools into existing CI/CD pipelines can be complex, particularly for organizations with legacy systems.
- Trust and Adoption: There may be resistance from developers or security teams to fully automate critical aspects of security, especially in industries with high compliance requirements.
6. Conclusion
The future of DevSecOps lies in autonomous CI/CD pipelines, where AI and ML work seamlessly to ensure continuous security throughout the software development life cycle. By automating security checks, identifying vulnerabilities in real-time and preventing threats before they impact production, AI/ML integration can drastically improve the security and agility of modern development practices.
As we move toward an increasingly automated software development world, organizations must embrace these technologies to stay ahead of evolving threats. Fully autonomous CI/CD pipelines not only enhance security but also accelerate the development process, allowing businesses to deliver secure software at the speed of innovation.




