Cycode, this week, added multiple artificial intelligence (AI) agents to its application security posture management (ASPM) capable of monitoring code and offering remediation suggestions.
In addition, the company is adding an ability to, in real-time, monitor continuous integration processes running in memory. That capability makes it possible to thwart, for example, recent attacks that exploited tj-actions files to compromise continuous integration/continuous delivery (CI/CD) infrastructure and developer credentials.
Amir Kazemi, director of product marketing for Cycode, said collectively these capabilities will enable DevSecOps teams to streamline DevSecOps workflows in a way that reduces the friction and chaos many of these teams currently encounter.
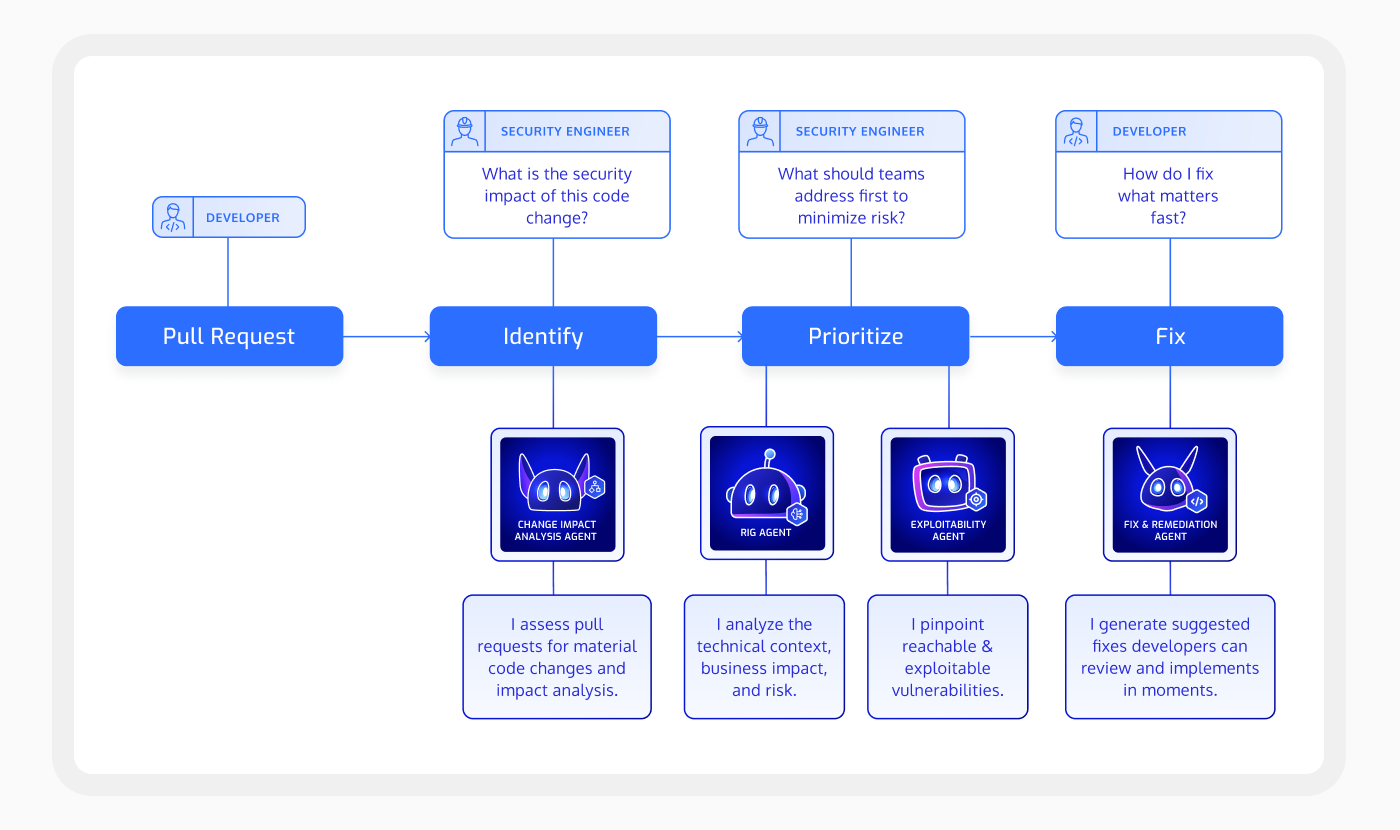
The agents being added between now and June to the Cycode platform, dubbed AI Agents, tap directly into a Risk Intelligence Graph (RIG) developed by Cycode to surface, for example, issues involving code repositories, workflows, secrets, dependencies and cloud infrastructure assets.
There is also a Change Impact Analysis Agent that monitors code changes across pull requests to identify material changes that significantly alter risk posture.
Finally, there is an Exploitability Agent that invokes the static application security testing (SAST) and source code analysis (SCA) scanning tools embedded in the Cycode platform, the results of which can be passed on to a Fix & Remediation Agent that analyzes the root cause of an issue to suggest code fixes that align with frameworks, coding patterns variable naming patterns being used by application development teams.
That ability to share data and context between agents is enabled by the Model Context Protocol (MCP), an emerging de facto standard integration framework for AI agents that was originally developed by Anthropic. MCP essentially functions as an operating system for AI agents, said Kazemi.
Longer term, Cycode also plans to leverage the agentic AI framework it has developed to build additional agents that can be assigned additional tasks, he added.
It’s not clear how rapidly DevSecOps teams are taking advantage of AI tools to improve application security, but as these technologies mature, there is a clear opportunity to improve application security without having to rely as much on cybersecurity teams to discover vulnerabilities in production environments that they hope application developers will have the time and expertise needed to fix. Instead, most issues will, hopefully, be surfaced and addressed long before that code is deployed.
The challenge, of course, will be not only finding the funding needed to acquire these AI tools, but also adjusting workflows to incorporate them. Many application development teams are relying on DevOps pipelines to build notoriously fragile applications. Improving the security of the software supply chain, however, may present an opportunity to address those issues and more as organizations look to securely deploy more applications at scale.
Regardless of motivation, there might soon come a day when deploying software that has known vulnerabilities becomes truly inexcusable when there is a cadre of AI agents standing at the ready to ensure only the code of the highest quality ever makes it into a production environment.




