Dynatrace has extended the Application Security Module it provides for its observability platform to protect against vulnerabilities in runtime environments, including the Java Virtual Machine (JVM), Node.js runtime and .NET CLR.
In addition, Dynatrace has extended its support to applications built using the Go programming language.
The Dynatrace Application Security Module leverages existing Dynatrace tracing and artificial intelligence (AI) technologies to detect threats in real-time and then apply appropriate policies to automatically secure applications. At the core of the Dynatrace approach to application security is its OneAgent software for application instrumentation, which collects data and feeds it back to an observability platform that includes an AI engine dubbed Davis.
Amit Shah, director of product marketing for application security at Dynatrace, said by extending the Application Security Module to support runtimes in the most widely adopted programming languages Dynatrace is now providing real-time visibility and vulnerability analytics across the entire application stack, which includes custom code, open-source and third-party libraries, language runtimes, container runtimes, and container orchestrators.
The Dynatrace platform not only identifies vulnerabilities across each of these layers automatically but also analyzes them to reduce false positives by only surfacing alerts concerning code that is actually running, noted Shah. Without those capabilities, it becomes impossible for development teams to prioritize their application remediation efforts in the absence of any context, he added.
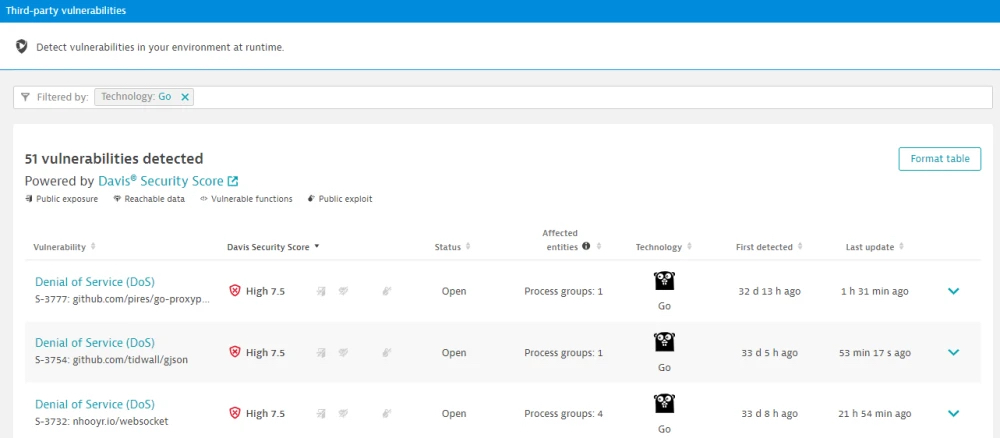
In general, achieving and maintaining application security will require more responsibility to shift both left and right, said Shah. While it’s critical to discover as many vulnerabilities as possible before applications are deployed it’s also crucial to make it simpler to discover vulnerabilities in runtimes after an application is deployed, he noted. The goal is to enable DevOps teams to employ the same observability platform they are using to manage and optimize applications to also ensure application security, Shah added.
That Dynatrace approach provides the added benefit of also avoiding the need to convene a “war room” to discover where all the vulnerabilities in those application environments might reside once they are discovered, Shah noted.
The primary application security challenge organizations face is the rate at which applications are now being deployed. Cybersecurity teams, because of a chronic shortage of talent and expertise, can’t keep pace. As a result, more responsibility for application security is being shifted left toward developers and DevOps teams as well as right toward IT and security operations teams. In effect, application security is finally becoming a team sport within IT organization as cybersecurity teams focus more of their efforts on securing runtime environments, noted Shah.
It may be a while before that approach has a major impact in terms of reducing the number of vulnerabilities being regularly introduced into application environments. However, as more tools and platforms that specifically address application security are deployed, the overall state of application security will steadily improve.
In the meantime, however, the volume of attacks aimed at the application layer of the IT stack will, unfortunately, continue to increase as cybercriminals focus more of their efforts on exploiting both now and zero-day application vulnerabilities that are increasing in volume with each passing day.





