Teleport today added an offering that makes it simpler to declaratively secure IT infrastructure and workloads using short-lived X.509 certificates.
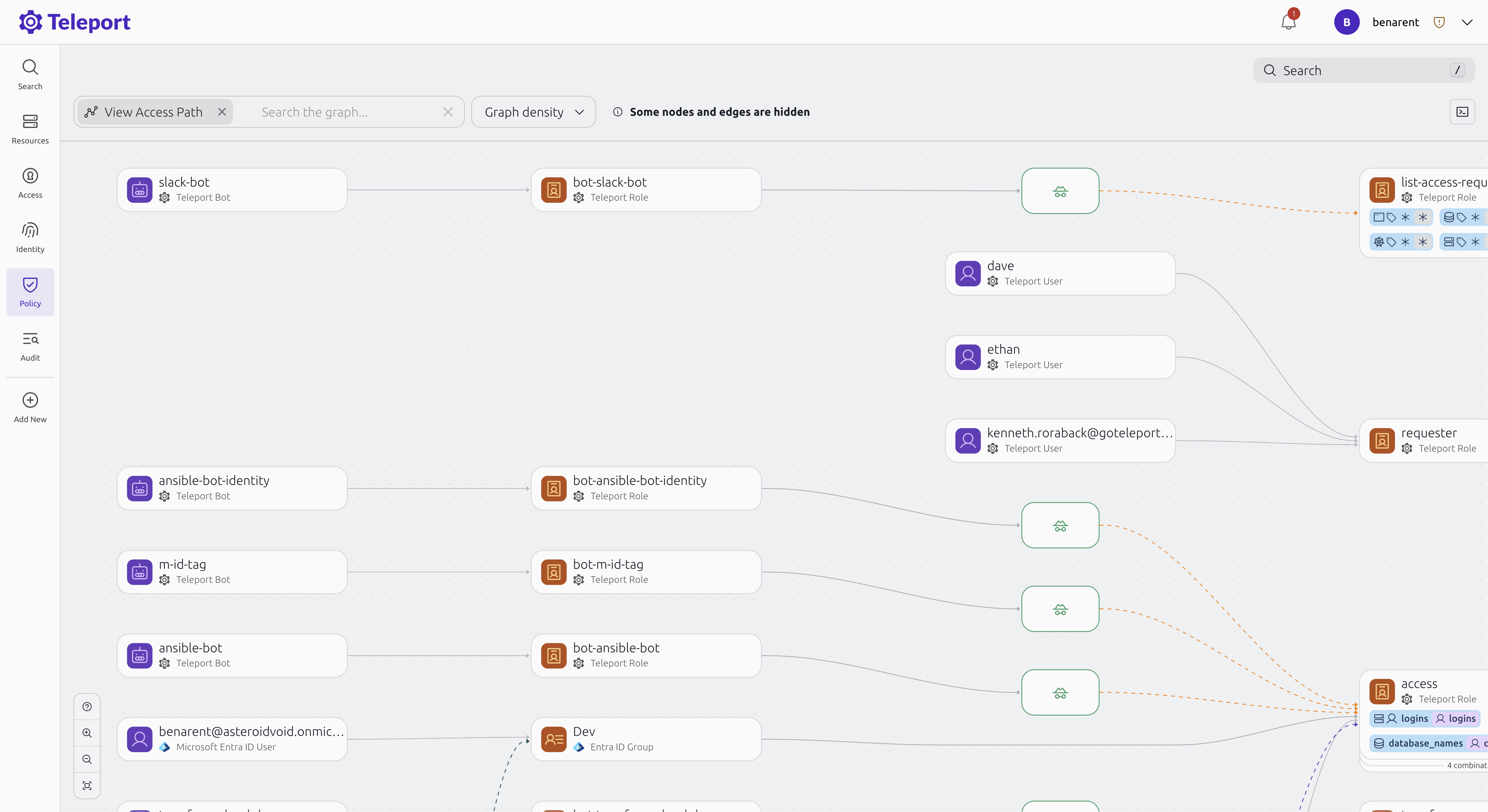
The Teleport Machine & Workload Identity platform is designed to unify the management of authentication, authorization and access control for non-human identities, in a way that eliminates reliance on static passwords, application programming interface (API) keys and application secrets that are easily compromised.
Teleport CEO Ev Kontsevoy said as IT environments become more dynamic it’s become apparent that enforcing zero-trust IT policies requires providing IT teams that provision infrastructure to deploy software a simpler way to consistently manage access, including the ability to discover existing machine and workload identities.
That’s critical because cybersecurity teams are only able to assess how policies are being enforced, he noted. It is DevOps and platform engineering teams that are responsible for initially providing access to the IT environment using programmatic tools that can easily result in misconfigurations, that can be avoided using a more declarative approach, Kontsevoy noted.
In furtherance of that effort, The Teleport Machine and Workload Identity platform also provides integrations with open policy agents, APIs, JSON Web Tokens (JWT) and Secure Production Identity Framework For Everyone (SPIFFE) frameworks.
Additionally, DevOps teams can apply fine-grained attribute-based and role-based access controls across a set of ephemeral authorization policies that can be dynamically applied as needed.
The Teleport Machine & Workload Identity also provides access to logs and exportable audit trails to make it simpler to comply with a wide range of regulatory frameworks.
Finally, the Teleport Machine & Workload Identity platform also provides a multi-region high availability option capable of scaling up to 140,000 connected resources across nine availability zones.
Much of the focus on implementing zero-trust IT policies has been on securing the credentials of end users. However, the IT infrastructure environment itself has remained comparatively insecure. Each element of the IT environment, including workloads, needs to be assigned an identity that can then be used to limit how much access can be gained through it, said Kontsevoy.
Cybercriminals have already proven they are extremely adept at exploiting and escalating privileges that they have found a way to access. Many of the breaches that have occurred in data centers can be traced back to access to a stolen credential. The challenge is the number of non-human identities involving, for example, application programming interfaces (APIs), that can potentially be exploited far exceeds the number that have been assigned to end users.
While a lot of effort has been clearly made to enforce best DevSecOps practices, the simplest thing for most organizations to improve software supply chain security is to apply more controls to how IT infrastructure is provisioned. The sad truth is that far too many application developers have access to far too many resources, using a set of passwords that have probably already been stolen multiple times over. The only way to address that issue is to eliminate the dependency on passwords as rapidly as possible. Otherwise, it’s not so much a question of whether an IT environment will be compromised but rather to what extent.




